SHA1:
- 71b1c32f89dcd3c2cbdb9f0e50685025f6f5f59b
- 75c24cc6bbfa89f5f4a622913f762b76dd7a24af
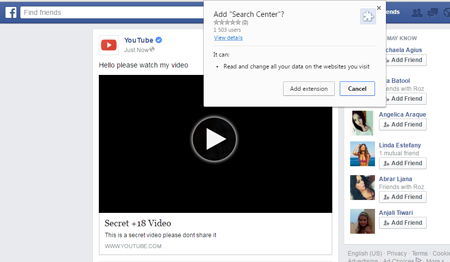
A malicious plug-in for Google Chrome that consists of three scripts written in JavaScript. If the user whose browser already contains this extension logs on to Facebook, this plug-in checks for “location.hostname”. If the value is not facebook.com, the script is terminated.
The Trojan retrieves uid from cookies and CSRF token from the social network webpage. Every 10 microseconds, it removes blocks with the following classes from the Facebook web interface:
- _5ce
- uiToggle wrap
- logoutMenu
- uiPopover
- UFICommentCloseButton
Then the Trojan creates a group named randomly. Using the group ID, the victim’s profile photo and the address of the webpage retrieved from a configuration file, the Trojan generates a “share a link” post and publishes it on the wall in specified intervals. What is more, in this post, the Trojan mentions all the victim’s friends on Facebook so this message is published on their walls too.
If the user follows the specified link, they are redirected to some webpage whose appearance is identical to the Facebook web design. Yet, if another website is used to follow this link, the user is redirected to a blank webpage. The webpage contains an allegedly standard video player. If the victim uses Chrome and tries to watch the video, they are prompted to download and install a browser plug-in. Trojan.BPlug.1074 can use this method to spread either its own copy or other plug-ins for Google Chrome.