- SHA1: 2d0a77fd005ca9a383f9c75e1484c2cdbd6261c4
Description
A trojan for iOS-based mobile devices. It is built into one of the imToken crypto wallet versions, modified by malicious actors. It steals mnemonic seed phrases used to access crypto wallets and sends them to the attackers’ server. To distribute the trojan, malware creators use specially created malicious websites that copy the appearance of imToken project’s genuine site. The malware is installed using configuration and provisioning profiles that allow downloading and installing apps outside the App Store..
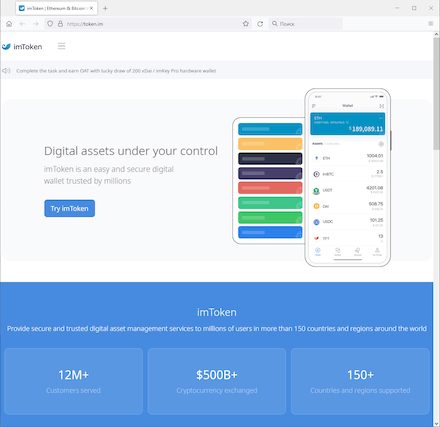
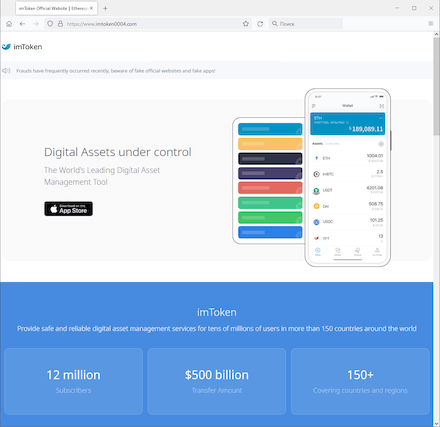
A comparison between the genuine website (left) and fake one (right):
Operating routine
The IPhoneOS.CoinSteal.1 is a full-fledged version of the imToken application with implanted malicious functionality. It looks and operates just like the original safe version. The data theft goes unnoticed by the users.
Upon launch, the trojan displays the app’s main menu. There, the user can either create new crypto wallets or import already existing ones.
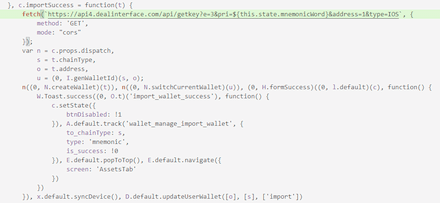
In both cases, the user has to enter their seed phrase for authorization into the corresponding field. At that, the seed phrase is covertly sent to the C&C server located at hxxps://api4[.]dealinterface[.]com/api/getkey.