SHA1 hash:
- 9b557feeb5a2e910b3261f31ebab1ac75d8651d4 (com.youmus)
Description
This trojan targets Android devices. When commanded by the C&C server, it changes its behavior and instead of providing the declared functionality, it loads in its window the contents of the target websites—most often an online casino. It uses the modified dnsjava library code, with whose help it receives a configuration from the malicious DNS server via a DNS request. Android.FakeApp.1669 is represented by various modifications that are disguised as different apps on distribution sources that include Google Play.
The following description of Android.FakeApp.1669’s operating routine is based on an analysis of the modification 9b557feeb5a2e910b3261f31ebab1ac75d8651d4.
Operating routine
When launched, the trojan sends a DNS request to the server 113[.]30.190[.]193, requesting a TXT record for the domain 3gEBkayjVYcMiztlrcJXHFSABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]simpalm[.]com.. The name of its sub-domain contains encoded data about the infected device. After decoding the prefix from the Base64 format, we get an array in which:
- the first 2 bytes — a constant;
- the next 4 bytes — a number, the first part of the id — the time of installation in the unix format;
- the next 8 bytes — a number, the second part of the id — a random number;
- the next 1 byte — the battery charge level;
- the next 1 byte — contains 2 flags: whether the battery is charging (0x40) and whether the developer mode is enabled (0x80);
- the next 2 bytes — a number, the screen width;
- the next 2 bytes — a number, the screen height;
- the next 20 bytes — a string, the model and brand of the device.
Note: numbers in this array are unsigned, big-endian.
Below is the data decoded from the above domain URL. For convenience, the parameter names are added and the JSON format is used:
{
"hardcoded_flag": -34,
"screen_width": 1080,
"screen_height": 2408,
"appsflyerUID": "1725178271111-903881458110846748",
"is_battery_charging": false,
"is_adb_or_dev_enabled": true,
"model_plus_brand": "SM-S721B/DSSamsung",
"batteryLevel": 84
}
The server response depends on the Internet connection type used on a device. If the connection is via target providers, including mobile Internet providers, the server will give the trojan the requested domain TXT record. In other cases, this record will not be provided.
The TXT record that the trojan receives has an encrypted configuration.
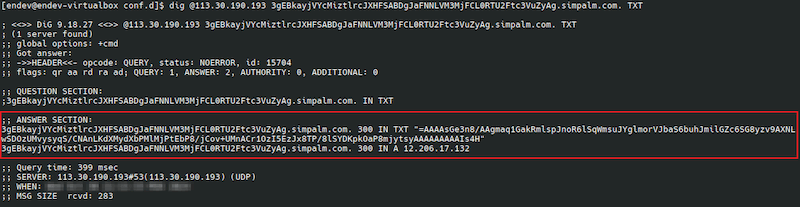
An example of a DNS server request using the dig program:
The contents of the record:
=AAAAsGe3n8/AAgmaq1GakRmlspJnoR6lSqWmsuJYglmorVJbaS6buhJmilGZc6SG8yzv9AXNLwSDOzUMvysyqS/CNAnLKdXMydXbPMlMjPtEbP8/jCov+UMnACr1OzI5EzJx8TP/8lSYDKpkOaP8mjytsyAAAAAAAAAIs4H
The following algorithm is used for decryption:
- string reversal;
- Base64 data decoding;
- gzip data decompression;
- line splitting using the character ÷.
The decrypted data:
url
hxxps[:]//goalachievplan[.]pro
af_id
DF3DgrCPUNxkkx7eiStQ6E
os_id
f109ec36-c6a8-481c-a8ff-3ac6b6131954
where:
- url — is the link that the trojan needs to open;
- af_id — an id for the AppsFlyer SDK analytical platform;
- os_id — an id for the OneSignal SDK push notification service.
Android.FakeApp.1669 loads the received link in WebView over its main interface. A chain of redirects starts from this web address to many intermediate sites, the last of which is an online casino site:
hxxps[:]//goalachievplan[.]pro?...
hxxps[:]//goalachievplan[.]pro/traf.php?...
hxxps[:]//offers[.]nsq[.]network/click?...
hxxps[:]//7000-promo[.]com/l/6577015f34b0985bf008581f?...
hxxps[:]//partners7redirect[.]com/?...
hxxps[:]//cda7k-ddok[.]com/cda/v2?...
hxxps[:]//7k476[.]casino/cda?...
hxxps[:]//7k476[.]casino/register?...
hxxps[:]//7k476[.]casino/en/register?...
As a result, instead of the expected functionality, the user sees the contents of the target site in the malware’s window.
If the trojan does not receive the TXT record from the malicious DNS server, it continues to operate as a normal application:
DNS requests to the C&C server from different trojan modifications
| Trojan package name | DNS server | Generated domain name | The contents of the domain TXT record |
|---|---|---|---|
| com.llx | 113[.]30.190[.]193 | 3gEBkayjVYcMiztlrcJXHFSABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]actionbutton[.]com. | ==AAAAwZFI7LtDwAYihWYuFGYW6mnkpmqnlpmaS6ZkJmauemkaqWpnBpZuZGmY6GLZwLP/2Dc1sALN4MTx8KzKrK9L0Acuo0dxI3dt9wUyM+0Ss9w/PKg+6X3UzNnUDLxiCp/+lSYDKpkOaP8mjytsyAAAAAAAAAIs4H |
| com.youmus | 113[.]30.190[.]193 | 3gEBkayjVYcMiztlrcJXHFSABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]simpalm[.]com. | =AAAAsGe3n8/AAgmaq1GakRmlspJnoR6lSqWmsuJYglmorVJbaS6buhJmilGZc6SG8yzv9AXNLwSDOzUMvysyqS/CNAnLKdXMydXbPMlMjPtEbP8/jCov+UMnACr1OzI5EzJx8TP/8lSYDKpkOaP8mjytsyAAAAAAAAAIs4H |
| com.amazon.avod.thirdparty | 113[.]30.190[.]193 | 3gEBkayjVYcMiztlrcJXHFTABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]revolt[.]digital. | ==AAAAga1lKGrDgAZWSGmQapnqhpZpppqbqpaaC6YVKGai+GZcqmpfCJbp5GYgxWLZwLP/2Dc1sALN4MTx8KzKrK9L0Acuo0dxI3dt9wUyM+0Ss9w/PKg+KWgOLJl+SM4sbO1MSO/8lSYDKpkOaP8mjytsyAAAAAAAAAIs4H |
| com.kumobius.android.wal | 113[.]30.190[.]193 | 3gEBkayjVYcMiztlrcJXHFSABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]somniosoftware[.]com. | =AAAAsGpbV/zAAAmZpBGZZSWaeSGZox6aiJWap+JaSqmrTimlY66acCJaphWks5SG8yzv9AXNLwSDOzUMvysyqS/CNAnLKdXMydXbPMlMjPtEbP81/yMn8yPvs1P/kjM3eDNyWbK/8lSYDKpkOaP8mjytsyAAAAAAAAAIs4H |
| com.amazon.avod.thirdpart | 113[.]30.190[.]193 | 3gEBkayjVYcMiztlrcJXHFTABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]dteam[.]dev. | ==AAAAAZ2lkYnAwAbuRGkuZJYaqJaplmqrlmmqV6aeKmaqeJmshJpbCpYaaGnkxpLZwLP/2Dc1sALN4MTx8KzKrK9L0Acuo0dxI3dt9wUyM+0Ss9w/PKg+6T10zP3UzN/8lSYDKpkOaP8mjytsyAAAAAAAAAIs4H |
| com.durakm.durak | 113[.]30.190[.]193 | 3gEBkayjVYcMiztlrcJXHFTABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]emizentech[.]com. | ==AAAAgaAsQVeDAAYq5mlkZmmQCpZqhWpn5paai6ZUCJaquWnuhJrvpGmc6mZq5WLZwLP/2Dc1sALN4MTx8KzKrK9L0Acuo0dxI3dt9wUyM+0Ss9w/PKg+aXvMDL/ejMxeCI4ObJ/8lSYDKpkOaP8mjytsyAAAAAAAAAIs4H |
| com.word.count | 113[.]30.190[.]193 | 3gEBkayjVYcMiztlrcJXHFTABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]mindsea[.]com. | AAAAp195YGHADgxpaohmZaqmZdCGaueJbQiWobqpkoJ6mm1GmsuGbUimYkhGbskBv88bPwVzCs0gzMFzrMrsq0vQDw5iS3Fjc312DTJz4TLx2D//oA6rABask8KN/mTJo8LP/+lSYDKpkOaP8mjytsyAAAAAAAAAIs4H |
| com.kumobius.android.walljum | 113[.]30.190[.]193 | 3gEBkayjVYcMiztlrcJXHFSABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]azikus[.]com. | ==AAAAgZAifV/5TlgGIFIPKQJbElNbBysS+SWmCOuchWv5O3xQTQ6Hj4X9cPufq62+mXtRdMQnPoGsD2EPMYux9ClSjyjvX3GuC23vteLcBg80M0qRCFU58Udgmiy8stSHqRZNB0AABIAqwSJ3xAAAAAAAAAIs4H |
| com.dessertdreams.recipes | 113[.]30.188[.]48 | 3gEBkayjVYcMiztlrcJXHFWABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]outorigin[.]com. | ==AAAAgaDqfMaAQAkkVpZQiWao5GZopGorhWZYS6acCmaqOGYVqJrvxmnohpapxmLZwLP/2Dc1sALN4MTx8KzKrK9L0Acuo0dxI3dt9wUyM+0Ss9w/PKg+KW3GTNoUKJoWLO4WbJ/8lSYDKpkOaP8mjytsy/CcGIE3BAIs4H |
| com.dualtext.compare | 113[.]30.188[.]48 | 3gEBkayjVYcMiztlrcJXHFSABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]halcyonmobile[.]com. | =AAAAUmALHs7AEwJlkRmlohJliBWkql6maiGaheGlSqmpjpWZZ66Yq1JlUaJnu5SG8yzv9AXNLwSDOzUMvysyqS/CNAnLKdXMydXbPMlMjPtEbP8/jCovSko1SypxQTp/8lSYDKpkOaP8mjytsy/CcGIEzNAIs4H |
| com.vivo.eas | 113[.]30.190[.]193 | 3gEBkayjVYcMiztlrcJXHFTABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]tridhyatech[.]com. | =AAAAUGhT/P/AMQmYgVpmmRplYKJYYa6nqZpmkemmilmrnhJnoh6auBmaZKJnu5SG8yzv9AXNLwSDOzUMvysyqS/CNAnLKdXMydXbPMlMjPtEbP8/jCovS0rxcCI0+rM/+lSYDKpkOaP8mjytsyAAAAAAAAAIs4H |
| com.fruitypic.editor | 113[.]30.190[.]193 | 3gEBkayjVYcMiztlrcJXHFTABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]qualhon[.]com. | |
| com.kumobius.android.wall | 113[.]30.190[.]193 | 3gEBkayjVYcMiztlrcJXHFTABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]fingent[.]com. | |
| com.alibaba.aliexpre | 113[.]30.190[.]193 | 3gEBkayjVYcMiztlrcJXHFTAAyoHDlNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]rakeingrass[.]com. | AAAADrxOwn7/OGNQAEGpFfXjhwRIkwOKcVWhsfJMMkiL6wYoKg0ZIWyKpbQlBjYxk1eEbV3yoYJ4HxaOqUoITxRRQIyKIY6R1mbLx9kS/LUTGuRf3/4LbYe05m7L9+Ta5y9SOFhpzuj3Zijg+Rg5n1Fmr5qeLrUXJP2i8fZE1ILUGe9lfzKJFj+BsytJlWCDh8xhN5aMjuko3eQnhMR4AhBMC6QSM3xAAAAAAAAAIs4H |
| com.score.time | 113[.]30.188[.]48 | 3gEBkayjVYcMiztlrcJXHFaABDgJaFNNLVM3MjFCL0RTU2Ftc3VuZyAg[.]wdipl[.]com. | AAAAmlKpbPGACcymaqZmaiBGYoFmatOmkilWqrZJkqZ6noJpahepkUqplcimbukBv88bPwVzCs0gzMFzrMrsq0vQDw5iS3Fjc312DTJz4TLx2D//oA6rVdzMkULK/mDO/+lSYDKpkOaP8mjytsy/CcWMOLHAIs4H |