SHA1 hash:
- 96bf2f07c785f6889799458f0609293ccb005634 (svc_host.exe)
Description
A malicious program written in the C++ programming language and designed to steal cryptocurrency from Microsoft Windows computer users. It substitutes crypto wallet addresses copied into the clipboard with ones belonging to the attackers.
Operating routine
Trojan.Clipper.808 is installed on target systems particularly by Trojan.Packed2.49862 malware, which contains the stealer in its body. The following internal file names of Trojan.Clipper.808 are known:
- Smoking_clipper.exe
- moreaddeasy.exe
- AdminControl.exe
Trojan.Clipper.808 as a payload in Trojan.Packed2.49862’s body
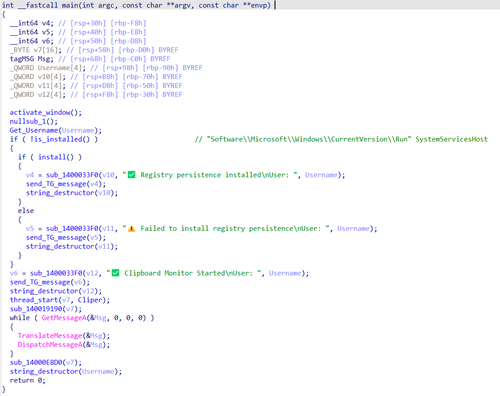
After launching, Trojan.Clipper.808 copies itself to %APPDATA%\systemservices\svc_host.exe and configures this file to run at system startup. For this, it creates a registry key Software\\Microsoft\\Windows\\CurrentVersion\\Run with the name SystemServicesHost.
Configuring the trojan file to run automatically at system startup
While in operation, Trojan.Clipper.808 monitors the clipboard and substitutes the crypto wallet addresses copied into it with ones belonging to malicious actors.
Some Trojan.Clipper.808 modifications use the SSPI UAC Bypass technique for system privilege escalation and also have the functionality needed to spread via the local network.
Logging its actions
Trojan.Clipper.808 informs the attackers about the results of its work by sending messages to a Telegram bot, using the Telegram API. These messages are sent when:
- the trojan is installed in the system and sends information about the computer (the device name, the user’s name, and the system version) to the attackers;
- crypto wallet addresses are substituted (the address for the original wallet and the substituted one are sent);
- it has successfully escalated its privileges;
- it has successfully copied the trojan file over the network.