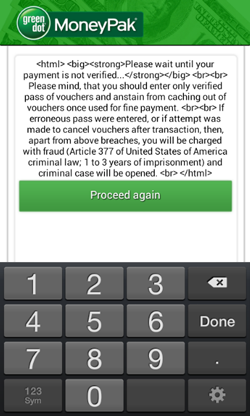
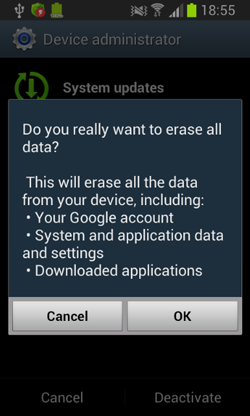
A ransomware program that locks Android devices and demands a ransome for their unlocking. Distributed under in the guise of a system update.
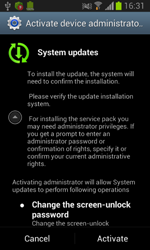
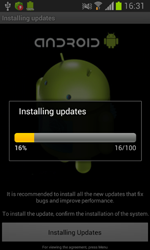
When launched, the program mimics updating progress and attempts to gain access to the device's administrative features, removes its icon from the home screen and awaits intruders' instructions.
 |
 |
 |
Control interface
Intruders facilitate control over the malware via SMS that may contain the following commands:
- set_lock – lock the device.
- set_lock – Unlock the device.
- send_sms – send an SMS.
- send_all – send SMS-messages to all contacts found in the phone book.
- set_admin – Specifies the phone number to send reports to.
- gitler_dead – remove itself.
- set_filtr – create a filter to intercept incoming messages.
- set_url – replace the address of the control server with one specified as the command parameter.
Lock device
Once the command set_lock, or a directive from a control server located at http://[xxx]tz.in/mod_admin/ is received, Android.Locker.38.origin locks the device and displays a ransom demand.
If the device's user attempts to revoke the administrative privileges from the malware, the locker will switch the device into the standby mode and once the lock screen is removed, it will display a false warning about the impending removal of all the data stored on the device.
When the user taps OK, Android.Locker.38.origin will switch the device to the standby mode again and set 12345 as the screen unlock password.
SMS-bot
The program can also send various messages whose recipients can include all the contacts available in the phone book.